About
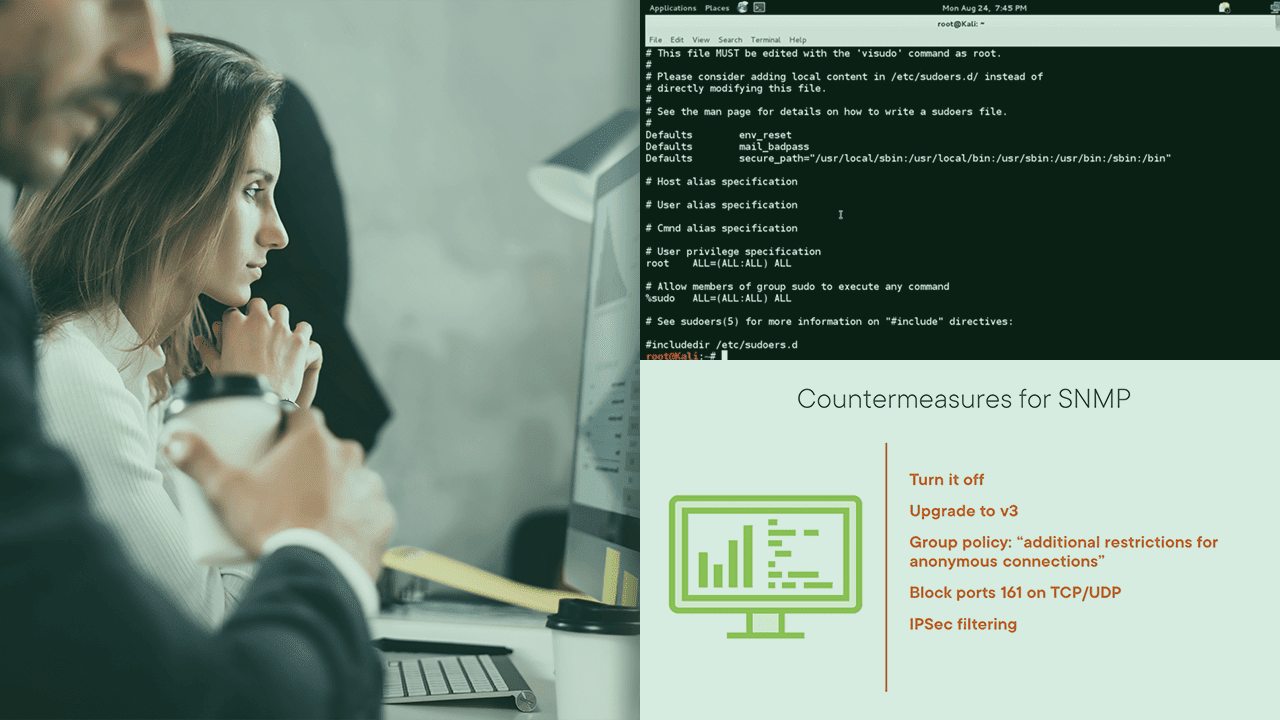
The third phase attackers perform on a target is enumerating accounts and services. This course will teach you skills attackers use for enumeration that needed for the Certified Ethical Hacking exam.
Description
To truly compromise a system, making sure you know what OS, accounts, and services that are running is key. In this course, Ethical Hacking: Enumeration, you’ll learn to identify accounts and services through enumeration. First, you’ll explore how to use NetBIOS to expose intel. Next, you’ll discover how to use LDAP to expose user accounts and other protocols to complete your enumeration tasks. Finally, you’ll learn the countermeasures to thwart enumeration attacks. When you’re finished with this course, you’ll have the skills and knowledge of enumeration techniques needed for the Certified Ethical Hacking exam.
Level
• Intermediate
About Author
Dale Meredith has been a Certified Ethical Hacker/Instructor EC-Council for the past 15 years, and Microsoft Certified Trainer for over 20 years. Dale also has an additional 7 years of senior IT management experience and worked as a CTO for a popular ISP provider. Dale’s expertise is in explaining difficult concepts and ensuring his students have an actionable knowledge of the course material.
Size: 348MB
Course: https://www.pluralsight.com/courses/enumeration-ethical-hacking-ceh-cert

